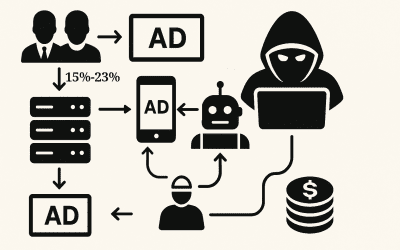
Digital Ad Fraud: Ruthless Tactics And Winning Strategies
Anatomy of Modern Ad Fraud Operations Fraudsters build elaborate infrastructure to impersonate both legitimate...
Supply Chain Security
Supply Chain Security: Protecting Against Third-Party Risks Supply chain security refers to the strategies and...
Mobile Device Security
Mobile Device Security: Protecting Data on the Go Mobile device security is essential in today’s digital age, as...
Identity and Access Management (IAM)
Identity and Access Management (IAM): Controlling Who Has Access Identity and Access Management (IAM) refers to the...
Defending Against LLMNR, mDNS, and NBT-NS Poisoning: A Practical Guide!
Why This Matters If you're an IT Administrator, CTO, CSO, or responsible for safeguarding your organization's network...
Data Backup and Recovery
Data Backup and Recovery: Ensuring Business Continuity Data backup and recovery are critical processes that ensure the...
Email Security
Email Security: Protecting Communications from Threats Email security refers to the techniques and tools used to...
Securing Internet of Things
Securing Internet of Things (IoT) Devices: Protecting the Connected World The Internet of Things (IoT) connects...
Remote Work Security
Remote Work Security: Protecting Your Business from Anywhere As remote work continues to grow, securing your business...
Cloud Security
What is Cloud Security? Cloud security refers to the set of practices, policies, and technologies designed to protect...