Why This Matters
If you’re an IT Administrator, CTO, CSO, or responsible for safeguarding your organization’s network infrastructure, you’ve likely encountered a penetration test report with the alarming message:
“We have gained access as Domain/Enterprise Administrators.”
This scenario is more common than many realize, often occurring within minutes through widely available tools. Attackers—whether cybercriminals or penetration testers—exploit weaknesses in network name resolution protocols to intercept credentials and escalate privileges within an organization.
Understanding the Security Threat Landscape
Cyber threats targeting corporate networks are increasing at an unprecedented rate. Organizations that fail to address weaknesses in Link-Local Multicast Name Resolution (LLMNR), Multicast DNS (mDNS), and NetBIOS Name Service (NBT-NS) expose themselves to significant risks. Attackers frequently use tools like Responder to intercept authentication attempts, steal credentials, and escalate privileges, often leading to full domain compromise.
The Business Risks
- Credential Theft: Attackers can capture authentication data and replay it for unauthorized access.
- Lateral Movement: Stolen credentials enable attackers to pivot within the network, gaining further control.
- Regulatory & Compliance Issues: Failure to mitigate these vulnerabilities may result in non-compliance with regulations such as PCI DSS, GDPR, SOC 2 and HIPAA, leading to fines and reputational damage.
- Business Continuity Disruptions: A security breach can cause downtime, data loss, and operational inefficiencies, ultimately affecting revenue and stakeholder trust.
How GWRX Group Can Help
At GWRX Group, we specialize in offensive security and penetration testing to proactively identify and remediate vulnerabilities before real-world attackers exploit them. Our customized security assessments provide actionable insights, helping organizations fortify their defenses against credential theft and unauthorized access.
📢 Don’t wait for a breach—schedule a security assessment today here!
Technical Deep Dive: Understanding the Attack and Mitigation
How Attackers Exploit LLMNR, mDNS, and NBT-NS
Adversaries exploit weak name resolution protocols to intercept credentials using tools like Responder. The attack generally follows these steps:
- Network Discovery: The attacker sets up Responder on a networked machine, passively listening for broadcast queries.
- Poisoning Responses: When a workstation requests a non-existent network resource, LLMNR, mDNS, or NBT-NS transmits a query.
- Credential Interception: The attacker’s machine sends a faster response, tricking the target into sending NTLMv2 hashes.
- Exploitation: The attacker either cracks the intercepted hashes to obtain plaintext passwords or uses them in pass-the-hash (PtH) attacks to access privileged systems.
- Privilege Escalation & Persistence: If successful, the attacker gains elevated access, allowing lateral movement and exfiltration of sensitive data.
Attack Timeline Breakdown
- 00:00 – 00:11: Responder initialized, awaiting vulnerable requests.
- 00:11 – 00:33: A workstation powers on, revealing its identity and network details.
- 00:33 – 01:44: Observing poisoned responses exploiting LLMNR, mDNS, and NBT-NS.
- 01:44 – 02:17: A user initiates a connection to a share (\test), triggering credential leakage.
- 02:17 – 03:22: A GPO is created to disable LLMNR.
- 03:22 – 04:10: The attack persists as NBT-NS remains enabled.
- 04:10 – 05:56: A registry key modification and PowerShell script disable NBT-NS.
- 05:56 – End: The system is rebooted twice to ensure NBT-NS is fully disabled.
Remediation Actions: Hardening Your Network
Disabling LLMNR (Link-Local Multicast Name Resolution)
Using Group Policy (GPO):
- Open the Group Policy Management Editor (
gpedit.msc). - Navigate to:
Computer Configuration > Administrative Templates > Network > DNS Client. - Locate Turn Off Multicast Name Resolution.
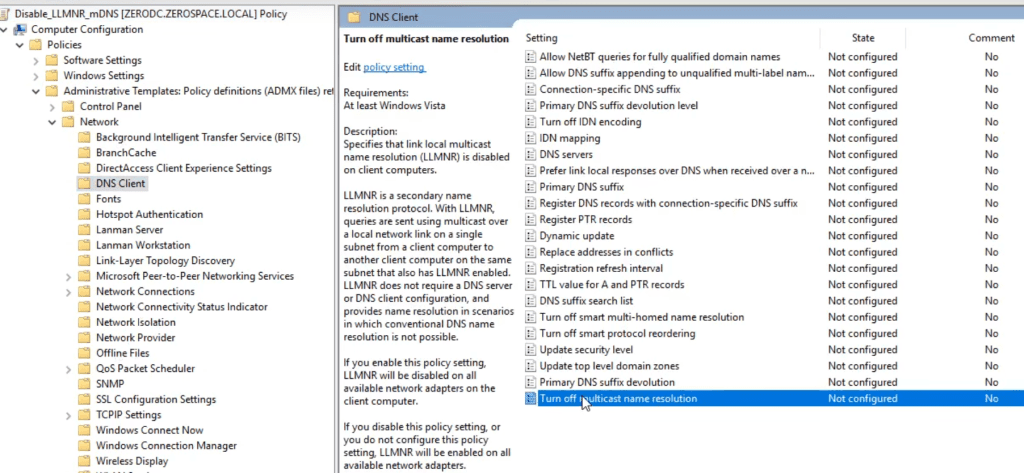
- Set it to Enabled.
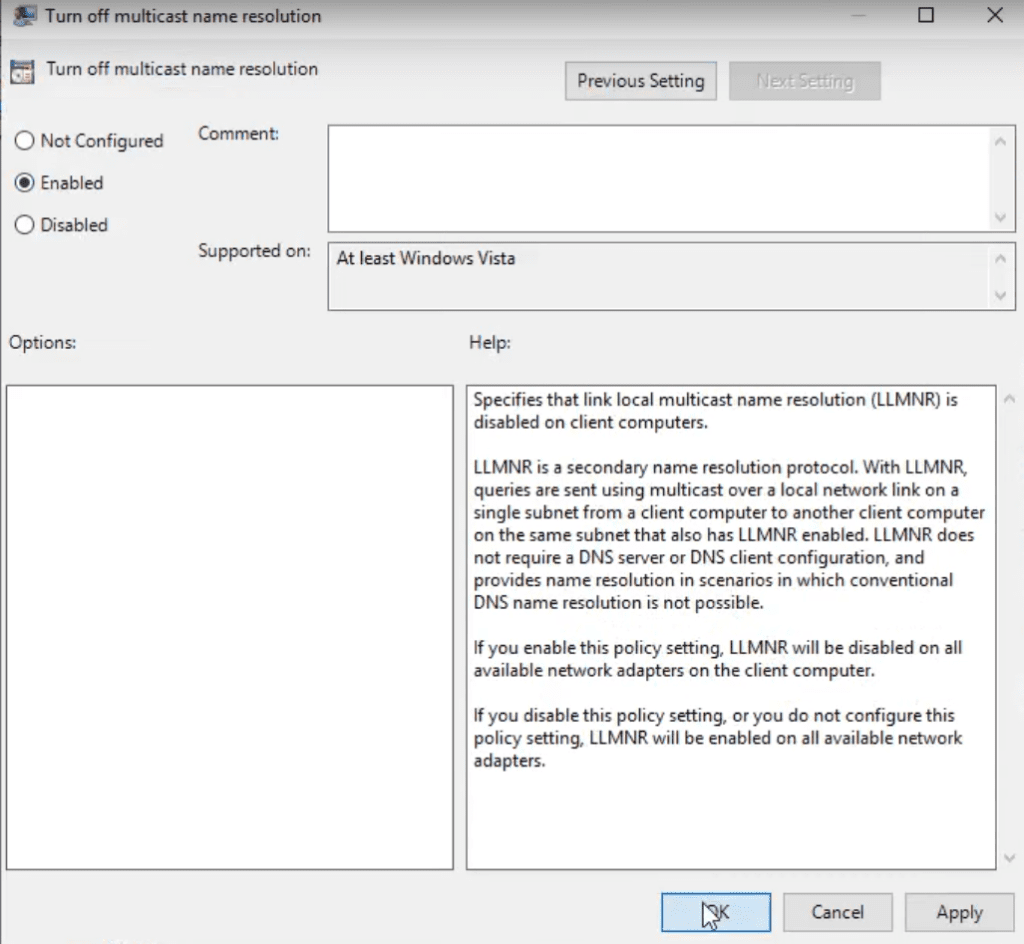
- Apply and enforce the policy across the domain.
This configuration prevents LLMNR name resolution attempts, reducing exposure to poisoning attacks.
Disabling mDNS (Multicast DNS)
Method 1: Using Registry Editor (Local Machine)
- Press Win + R, type
regedit, and press Enter. - Navigate to:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Dnscache\Parameters - In the right pane, right-click and select New > DWORD (32-bit) Value.
- Name the new value: EnableMDNS.
- Set its value to
0(zero) to disable mDNS. - Restart the computer for the changes to take effect.
This method configures the DNS Client service to disable mDNS for name resolution.
Method 2: Using Group Policy (Domain-Wide Deployment)
- Open Group Policy Management Console (
gpmc.msc). - Create a new Group Policy Object (GPO) or edit an existing one.
- Navigate to:
Computer Configuration > Preferences > Windows Settings > Registry. - Right-click and select New > Registry Item.
- Configure the registry item with the following settings:
- Action: Update
- Hive: HKEY_LOCAL_MACHINE
- Key Path:
SYSTEM\CurrentControlSet\Services\Dnscache\Parameters - Value Name:
EnableMDNS - Value Type:
REG_DWORD - Value Data:
0
Link the GPO to the appropriate Organizational Unit (OU) to apply the settings across multiple machines.
This approach allows administrators to efficiently disable mDNS on all domain-joined machines.
Disabling NBT-NS (NetBIOS Name Service)
To disable NBT-NS, you must disable NetBIOS over TCP/IP.
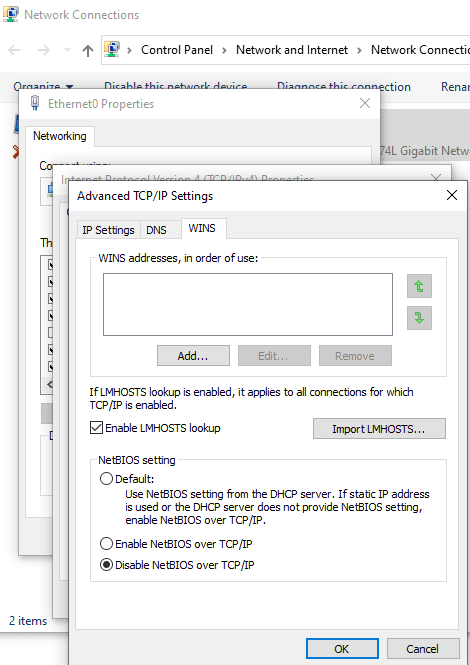
Method 1: Manually (For a Single Workstation)
- Open Network and Sharing Center.
- Click on Change adapter settings.
- Right-click on the active network adapter and select Properties.
- Select Internet Protocol Version 4 (TCP/IPv4) and click Properties.
- Click Advanced, go to the WINS tab.
- Under NetBIOS setting, select Disable NetBIOS over TCP/IP.
- Click OK and restart the system.
Method 2: Using PowerShell Script (For Multiple Machines)
For large-scale deployments, updating registry values is required to disable NBT-NS across all network interfaces. Use the following PowerShell script to automate this:
PowerShell Script: disableNetbios.ps1
$regkey = "HKLM:SYSTEM\CurrentControlSet\services\NetBT\Parameters\Interfaces"
Get-ChildItem $regkey | ForEach-Object {
Set-ItemProperty -Path "$regkey\$($_.PSChildName)" -Name NetbiosOptions -Value 2 -Verbose
}This script modifies the NetbiosOptions registry value to 2, disabling NBT-NS.
Method 3: Deploy via Group Policy (GPO)
To ensure this script runs on all workstations automatically:
- Open Group Policy Management Console (
gpmc.msc). - Create a new GPO or edit an existing one.
- Navigate to:
Computer Configuration > Policies > Windows Settings > Scripts (Startup/Shutdown). - Click Startup, then Add the
disableNetbios.ps1script. - Link the GPO to the target Organizational Unit (OU).
Important Considerations
- First Reboot: The PowerShell script runs and modifies the registry keys, but NBT-NS is not fully disabled yet.
- Second Reboot: The changes take full effect after the network adapters are restarted or the system is rebooted again.
During the window between the first and second reboot, NBT-NS attacks remain possible. Therefore, organizations should plan to enforce an additional restart as soon as possible to complete the remediation process.
Considerations Before Disabling WINS/NetBT
Before deactivating WINS/NetBT name resolution, confirm that your network does not rely on legacy applications that require these services. WINS/NetBT may still be necessary for:
- Windows Server 2003, XP, or 2000 environments that depend on DNS-based name resolution.
- Older operating systems such as Windows NT, Windows Millennium Edition, Windows 98, and Windows 95, which may require WINS for proper network functionality.
For further details, refer to: Microsoft Documentation
References
In the following repository you can find the script which is presented in the video and a Powershell script which automates the creation of the GPO:
For further details and implementation scripts, refer to the following resources:
- Microsoft Troubleshooting Guide
- Technet PowerShell Group Policy Startup/Shutdown Scripts
- Windows Protocols Documentation
Conclusion
Disabling LLMNR, mDNS, and NBT-NS is a crucial security enhancement for enterprise environments. While deactivating these services requires careful planning—especially in networks running legacy systems—the risks of keeping them enabled far outweigh the temporary operational challenges.
At GWRX Group, we specialize in assessing, mitigating, and securing enterprise environments against modern cyber threats. If you seek to validate your security posture or require assistance in implementing these defenses, contact our experts today.
📢 Stay ahead of cyber threats—protect your credentials, secure your network, and fortify your business!
Don’t wait for a breach—schedule a security assessment today here!
.
